-->
- Windows AppLocker allows administrators to control which executable files are denied or allowed to execute. With AppLocker, administrators are able to create rules based on file names, publishers or file location that will allow certain files to execute.
- The right click on Windows logo launches a menu? Well, your lock is problably due to the Applocker. AppLocker helps you control which apps and files users can run. These include executable files, scripts, Windows Installer files, dynamic-link libraries (DLLs), packaged apps, and packaged app installers.
Applies to
- Windows 10
- Windows Server
This application is for all the people who wants to make their apps password protected. This app covers all the major social networking apps to add extra layer of protection. Just setup the password on first time launch and make your desired app password protected. Hi Sergey, You can only manage AppLocker with Group Policy on devices running Windows 10 Enterprise, Windows 10 Education. If you want to restrict applications on other user account, we could add those applications to registry HKEYCURRENTUSER SOFTWARE Microsoft Windows CurrentVersion Policies Explorer DisallowRun.
This topic for the IT professional describes what AppLocker is and how its features differ from Software Restriction Policies.
AppLocker advances the app control features and functionality of Software Restriction Policies. AppLocker contains new capabilities and extensions that allow you to create rules to allow or deny apps from running based on unique identities of files and to specify which users or groups can run those apps.
Using AppLocker, you can:
- Control the following types of apps: executable files (.exe and .com), scripts (.js, .ps1, .vbs, .cmd, and .bat), Windows Installer files (.mst, .msi and .msp), and DLL files (.dll and .ocx), and packaged apps and packaged app installers (appx).
- Define rules based on file attributes derived from the digital signature, including the publisher, product name, file name, and file version. For example, you can create rules based on the publisher attribute that is persistent through updates, or you can create rules for a specific version of a file.
- Assign a rule to a security group or an individual user.
- Create exceptions to rules. For example, you can create a rule that allows all Windows processes to run except Registry Editor (Regedit.exe).
- Use audit-only mode to deploy the policy and understand its impact before enforcing it.
- Import and export rules. The import and export affects the entire policy. For example, if you export a policy, all of the rules from all of the rule collections are exported, including the enforcement settings for the rule collections. If you import a policy, all criteria in the existing policy are overwritten.
- Streamline creating and managing AppLocker rules by using Windows PowerShell cmdlets.
AppLocker helps reduce administrative overhead and helps reduce the organization's cost of managing computing resources by decreasing the number of help desk calls that result from users running unapproved apps
Applocker Windows 10 Download
For information about the application control scenarios that AppLocker addresses, see AppLocker policy use scenarios.
What features are different between Software Restriction Policies and AppLocker?
Feature differences
Applocker Windows 10 Pro Download
The following table compares AppLocker to Software Restriction Policies.
| Feature | Software Restriction Policies | AppLocker |
|---|---|---|
Rule scope | All users | Specific user or group |
Rule conditions provided | File hash, path, certificate, registry path, and Internet zone | File hash, path, and publisher |
Rule types provided | Defined by the security levels:
| Allow and deny |
Default rule action | Unrestricted | Implicit deny |
Audit-only mode | No | Yes |
Wizard to create multiple rules at one time | No | Yes |
Policy import or export | No | Yes |
Rule collection | No | Yes |
Windows PowerShell support | No | Yes |
Custom error messages | No | Yes |
Application control function differences
The following table compares the application control functions of Software Restriction Policies (SRP) and AppLocker.
| Application control function | SRP | AppLocker |
|---|---|---|
Operating system scope | SRP policies can be applied to all Windows operating systems beginning with Windows XP and Windows Server 2003. | AppLocker policies apply only to those supported operating system versions and editions listed in Requirements to use AppLocker. But these systems can also use SRP. Note Use different GPOs for SRP and AppLocker rules. |
User support | SRP allows users to install applications as an administrator. | AppLocker policies are maintained through Group Policy, and only the administrator of the device can update an AppLocker policy. AppLocker permits customization of error messages to direct users to a Web page for help. |
Policy maintenance | SRP policies are updated by using the Local Security Policy snap-in or the Group Policy Management Console (GPMC). | AppLocker policies are updated by using the Local Security Policy snap-in or the GPMC. AppLocker supports a small set of PowerShell cmdlets to aid in administration and maintenance. |
Policy management infrastructure | To manage SRP policies, SRP uses Group Policy within a domain and the Local Security Policy snap-in for a local computer. | To manage AppLocker policies, AppLocker uses Group Policy within a domain and the Local Security Policy snap-in for a local computer. |
Block malicious scripts | Rules for blocking malicious scripts prevents all scripts associated with the Windows Script Host from running, except those that are digitally signed by your organization. | AppLocker rules can control the following file formats: .ps1, .bat, .cmd, .vbs, and .js. In addition, you can set exceptions to allow specific files to run. |
Manage software installation | SRP can prevent all Windows Installer packages from installing. It allows .msi files that are digitally signed by your organization to be installed. | The Windows Installer rule collection is a set of rules created for Windows Installer file types (.mst, .msi and .msp) to allow you to control the installation of files on client computers and servers. |
Manage all software on the computer | All software is managed in one rule set. By default, the policy for managing all software on a device disallows all software on the user's device, except software that is installed in the Windows folder, Program Files folder, or subfolders. | Unlike SRP, each AppLocker rule collection functions as an allowed list of files. Only the files that are listed within the rule collection will be allowed to run. This configuration makes it easier for administrators to determine what will occur when an AppLocker rule is applied. |
Different policies for different users | Rules are applied uniformly to all users on a particular device. | On a device that is shared by multiple users, an administrator can specify the groups of users who can access the installed software. Using AppLocker, an administrator can specify the user to whom a specific rule should apply. |
Related topics

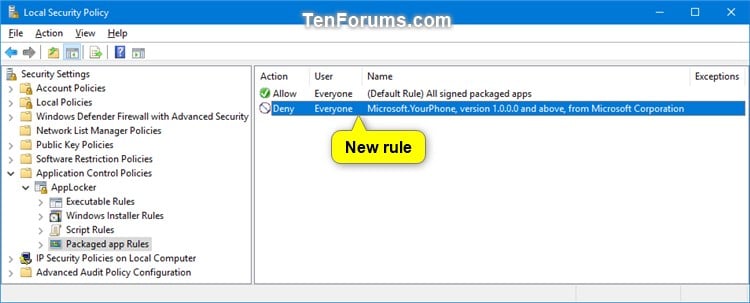
If you’re managing a fleet of computers in a business, you may not want users being able to access everything in the Microsoft Store. Having users a few clicks away from installing ‘Slotomainia’ or ‘Ninja World’ might not be what you want readily available on a business computer. You may also not want other services that can contribute to data leakage, or shadow IT type solutions that users decide to adopt.
As long as you are running Windows 10 Enterprise or Education, you could completely disable the Microsoft Store functionality by either using Applocker to maintain a whitelist of allowed packaged apps, or using Group Policy to enable the “Turn off Store application” under Computer Configuration > Administrative Templates > Windows Components.
For Windows 10 Pro and Home users, this won’t work so you’ll have to try other methods such as uninstalling Windows Store on each PC with the PowerShell command Get-AppxPackage *windowsstore* | Remove-AppxPackage
Disabling the Microsoft Store entirelybut you may find that there is a requirement to use a few of the Microsoft Store apps by your users. For this option (again just for Enterprise and Education, and you’ll need Office 365 or Azure AD), you can instead have a Private Store. This is enabled again in Group Policy, using the setting “Only display the private store within the Microsoft Store app” again under Computer Configuration > Administrative Templates > Windows Components.
The Microsoft Store will look pretty bare at this stage (I see the 5 apps in the screenshot below by default), so you’ll want to add or remove some apps. This is done online, Enterprise customers go to https://businessstore.microsoft.com and education customers go to https://educationstore.microsoft.com. You’ll need to sign in with an account that’s an Azure AD or Office 365 Global Administrator, but can then grant access to others.
To add an app, under ‘Shop for my group’ you can search or click through options to find the app you’re after – I’ve chosen Microsoft To-Do for this example. Going onto the app’s page will give you a button that says ‘Get the app’. Once you click that, you’ll see the message “Microsoft To-Do has been purchased and added to your inventory.” After you’ve done that, go to the “Manage” tab and then the “Products and Services” option on the right hand side. Find the app, click the ellipsis (…) and choose “Add to private store”
Applocker Windows 10 Professional
You will finally see a message saying that the app has been added to your store, but may take up to 36 hours* to show.
There’s also the option to assign an app to a user, this is only needed if it’s a licensed or paid for app that you want to give only to certain users – you may have bought 10 copies of a particular Windows Store app and need to control who has access to it.
Applocker Csp Windows 10 Pro
It’s worth having a look through the other options on this page as you can control settings such as letting users make purchases, what your organisation will be called in the Microsoft Store app and if you get invoices for the store via email.
Overall the Private Microsoft Store is rather easy to set up, lets you give users self-service access to apps that you allow, and gives you an easy way of letting someone install a Microsoft Store app in the future without having to enable the entire store.
Configure Applocker Windows 10 Pro
*Update 2nd August 2018
Windows 10 App Lockers
There’s been a great improvement to the 36 hour wait, it’s now within 15 minutes! More details here